Secure your Network with a Defense In-Depth Cybersecurity Strategy
As IT systems get more complicated, Cybersecurity threats become exponentially more aggressive. With a constant stream of Phishing, credential harvesting, Sim Jacking, Ransomware, and other email-borne attacks that can easily overwhelm a user's ability to detect, relying on Antivirus Software is often woefully ineffective against these attacks. In most cases, your firewall is just like a lock on the screen door to your house against a determined burglar at night.
Similar to the layers of a police officer's bulletproof vest, which utilizes multiple layers of Kevlar fabric to stop a bullet from penetrating his body, you need to weave numerous layers into your business' cybersecurity strategy.
The Use of a Defense In-Depth Cybersecurity Strategy Assures Network Security by Working based on the Following Principles:
Defenses in Multiple Places:
Using coordinated, organized, multiple security measures to keep your network safe is based on a military principle that a multi-layered and complex defense is more difficult to defeat than a single-barrier protection system. Many viruses can attack the network system from multiple points, so you must deploy robust defense mechanisms at various locations that can endure all types of attacks.
Your Network's Edge:
By deploying a more modern security appliance at your network's edge that incorporates intrusion prevention and detection (IPS/IDS) that can also employ a network reputation, geo-blocking ruleset coupled with enough CPU power to endure active network attacks you can make it easier for the other defense layers to do their respective jobs. Most attacks emanate from Russia and China so blocking traffic from those sources is a pretty good start.
Multiple Defense Layers:
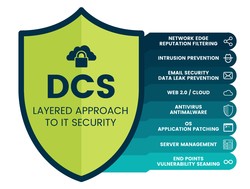
Defense in depth goes beyond just having a physical security system. It is a highly effective countermeasure strategy because it deploys multiple layered defense mechanisms between the attacker and its target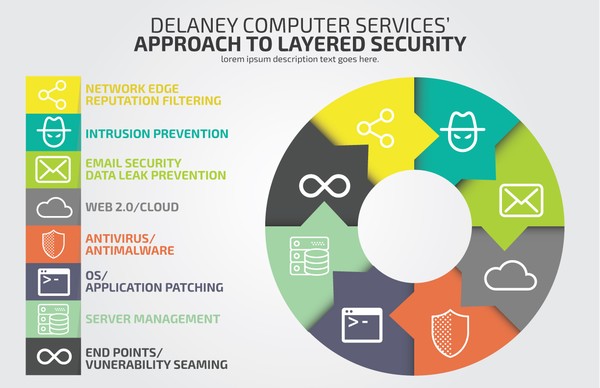 . Each layer of the defense has its unique mechanisms to withstand the virus attacks. Furthermore, it would be best to make sure that each layer has both detective and protective measures to ensure the network's security.
. Each layer of the defense has its unique mechanisms to withstand the virus attacks. Furthermore, it would be best to make sure that each layer has both detective and protective measures to ensure the network's security.
The reason for wrapping the network with multiple layers of defense is that a single protection line may be flawed. And the surest way to protect your system from any attacks is to deploy a series of different defenses to cover the weaknesses inherent in each of the individual defenses. Malware scanners, firewalls, intrusion detection systems, biometric verification, and local storage encryption tools can individually serve to protect your IT resources in a way others cannot. If you're looking to give your computer systems better protection against the harmful elements that the internet can bring, then give us a call, and we'll have one of our cybersecurity professionals speak to you about what we can do to defend your business.
Education and Ongoing Cybersecurity Awareness Training is a Must
The most important and what should be your first layer of defense is your Human Firewall. This is really your first and most effective defense layer. DCS makes cybersecurity awareness training for our client's employees mandatory and you should too. Users will learn how to spot and identify common cyber threats, and other email-borne phishing scams. Email has quickly become the largest threat vector and is your weakest link in a lot of cases. Most likely, your largest point of entry for a virus next to web surfing. Your employees need to learn how not to compromise computer systems' integrity with potentially unhealthy computer practices. As much as possible, teach them the dos and don'ts of using the computer, as well as how they can prevent viruses and other computer malware from coming in and destroying your system.
Get Away from the Break/Fix Approach to Managing your Company's Technology - Use a Managed Service Provider
Using an "IT Guy" to maintain your computer network is outdated and can cause more problems than they solve. Typically something has to break or stop working before your IT guy knows about it and you receive service, resulting in an inevitable reduction in IT system performance. At the same time, you wait for the problem to be fixed.
If you fall behind in keeping up with important tasks like backups, patches, and security updates, the odds greatly increase that you'll face an IT outage or another problem very quickly, which often leads to substantial productivity and revenue losses, which small business owners don't often take into account.
The most noticeable benefit of using a Managed Services Provider is since they use tools to monitor and maintain your network, they can often discover and fix problems before they can negatively affect your business. Still, they also do the hard, tedious. Boring work of keeping up with network monitoring, patch management, and desktop optimization performed regularly, which are all essential parts of the Defense In-Depth security model. Besides, the likelihood that your friendly neighborhood MSP has great techniques that your current IT guy may not know how to access.