New Ransomware, LOCKY, Emerges as Major Threat

Over the past few weeks, there has been a rise in reporting of a new crypto Ransomware called LOCKY. This new type of malicious ransomware is as straightforward as they come— gaining access to systems via unsolicited email attachments.
All of the reports have been the same thus far:
The user receives an email with a similar title to “ATTN: Invoice J-98223146” and a message such as "Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice":
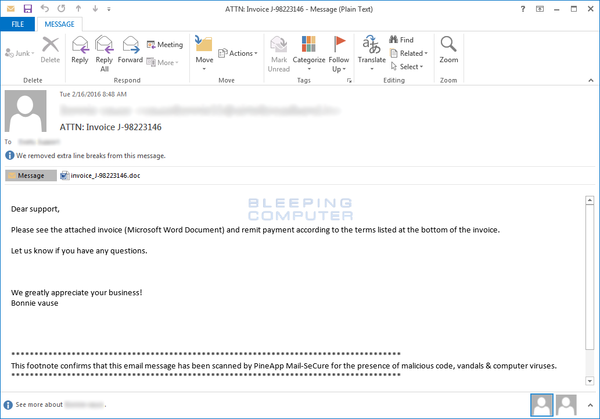
Locky email capture via bleepingcomputer.com
At first glance, the attachment appears to be a harmless Microsoft Word document; but as we’ve written about previously, this is a highly effective way for hackers to trick you into downloading their ransomware onto your own computer. Teaching your employees to err on the side of caution, especially with suspicious email attachments, is a top preventative measure when it comes to cyber security.
Once the attachment is opened, the document contents will appear as jumbled text. The document will instruct the confused user to “enable macros if the data encoding is incorrect”, prompting many to follow these malicious instructions:
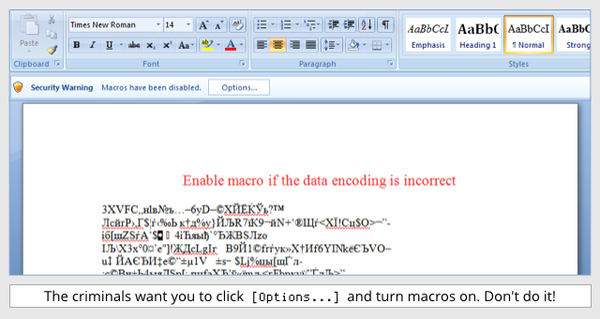
Locky email attachment capture via nakedsecurity.sophos.com
Unfortunately, this is when the ransomware takes hold of your computer. Locky will scan all local drives and unmapped network shares in search of files to encrypt. Locky will then encrypt essentially all of your files:
.mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11( Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat
After the installation process has completed, you will notice that Locky will rename all of your files in a new format [unique_id][identifier].locky (or something similar to F67091F1D24A922B1A7FC27E19A9D9BC.locky). All of your files are now inaccessible, and any Shadow Volume Copies (backups stored locally) cannot be used to restore the affected files.
You will also notice that Locky has downloaded ransom notes called _Locky_recover_instructions.txt within each folder where a file was encrypted, as well as applying the message as your desktop image, seen below:
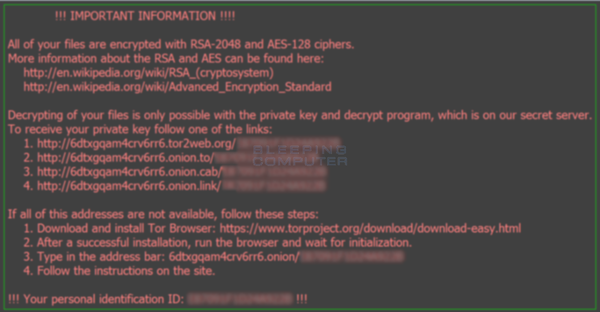
Locky desktop wallpaper capture via bleepingcomputer.com
If the ransom is paid, Locky will provide the user with a decryption key. This key will allow you to regain access to your files and systems as if nothing happened at all. “Cyber criminals will honor their "code" and release data after the payment, as it sets a precedent for future crimes, Epstein said, noting that some will even offer customer support to ensure the transaction goes smoothly.”
How To Avoid Locky
While Locky is certainly a malicious and dangerous form of crypto ransomware, there are ways to avoid it. Businesses need to take virtual threats seriously which must happen in the form of layered security.
First and foremost, educating yourself and your employees on the importance of email security is the very first and one of the most important preventative measures we can suggest. If you can train your employees to “think before they click”, you might avoid this virus all together. Additionally, employees can utilize the following precautionary measures to enhance their email security:
- Block mails with DOC, XLS or PDF attachments which contain macros
- Configure a setting which prompts the user before Office runs a macro
- Block access to Tor nodes
- Use browser/email AD blocking
While it is important to take some of these simpler security measures, we recommend getting a complete IT assessment to ensure that you have implemented a secure, layered approach to IT security. It’s never smart to roll the dice when it comes to cyber security, and applying a multi-layered tactic to fighting potential cyber threats is the only way to remain safe in this ever changing threatscape. These viruses can hit and infiltrate many areas of a specific computer and/or a network and have many tactics to do so. Having one approach is not enough. Antivirus alone cannot protect you from these attacks!
Delaney Computer Services would be happy to provide your SMB with an in-depth, hands-on IT assessment. We deliver a comprehensive 360-degree view of the current state of your IT infrastructure, utilizing industry-leading tools, physical inspections with over 20 years of experience in the world of IT. Through this assessment, we can help secure your business and eliminate the possibility of a cyber crime against your business.
